Just a few short years ago, virtual private networks (VPNs) were a novel technology to the masses. The advanced security and anonymity they offered were only for paranoids and dissidents. Fast forward to today’s internet with its daily headlines of massive data breaches, government snooping, and a Dark Web with an endless appetite for your personal information.
Suddenly, using a VPN doesn’t seem like such a radical concept.
A VPN Under the Hood
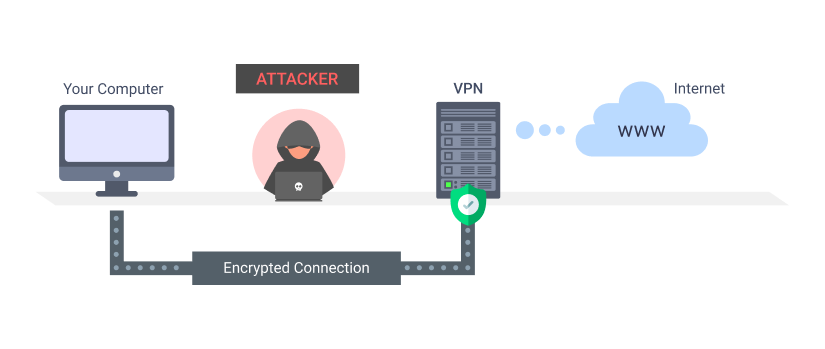
A VPN is used in conjunction with your internet service provider (ISP) and establishes a secure “tunnel” by which you connect to the internet. All data that leaves or returns to your computer is encrypted, which means no third-party hackers can identify either where you are physically located or the contents of the information related to the device you’re using.
You’re probably familiar with the way a firewall protects sensitive data on your computer. A VPN protects data once it leaves your computer and as you interact with the internet or remote networks.
A VPN creates a network of virtual P2P connections that hides your physical location and doubles down by encrypting your data. Even if a bad actor managed to pry some of your data loose they would still have to break a high-level encryption to be able to read it. Not likely.
The Problem of Leaks
Even though all VPNs are developed for the purpose of providing safe and private connections, not all of them are created equal; in some cases, buggy VPNs can leak data such as internet protocol (IP) addresses and even facilitate certain types of cybercrime.
Checking your VPN for data leaks is a crucial step of personal and business data security. One of the reasons VPN data leaks happen is because development of these privacy solutions is complex. Similar to the Windows operating system, many aspects of computing must be taken into account. A single overlooked issue related to a browser, firewall or third-party application that connects to the internet can cause VPN connection problems.
Here are some recommendations to help you check your VPN for leaks.
Basic Testing
Activating a VPN is as easy as downloading and installing software from the service. But how do you know the connection is secure? The bad news is that advanced testing requires a considerable amount of technical proficiency to get the setup right and deploy the appropriate tool suite.
The good news is that anyone with the skill set to simply log onto the internet can use a testing website (such as ipleak.net) that checks for leaks related to DNS, IP address, and WebRTC - we’ll talk about these terms along the way. While a testing website won’t catch every leak, it detects enough of them to make it a useful tool for the layperson.
VPN Leaks: It’s easy to test for active VPN leaks. Just activate your VPN, go online, and visit a testing website. A series of tests will be automatically performed. The results will let you know if any leaks were found.
The next step is to manually interrupt the connection while your VPN is running. Either unplug the ethernet or kill the WiFi signal. Count to 10 and reconnect, then visit a few different testing sites to see if any leaks are detected.
The results will let you know if any leaks found are related to DNS, IP address, or WebRTC. As mentioned, this isn’t the definitive way to thoroughly test the security of your connection, but in the absence of no tests at all, it’ll do.
How WebRTC Can Compromise VPN Connections
We promised to talk about WebRTC, so here it is.
Web Real-Time Communication is a relatively new open-source protocol and technology developed through an initiative launched by Google about seven years ago. The intent of WebRTC is to implement Voice over Internet Protocol (VoIP) technology directly on web browsers and without the need to install third-party apps.
For example, a company that enables WebRTC from its website can conduct job interviews without instructing applicants to install Skype or WhatsApp; another example would be taking customer service video conference calls right from the browser.
Peer-to-peer communications protocols are necessary with WebRTC connections. Part of the initiation process in WebRTC sessions requires the creation of certain channels between the facilitating website and the browser.
These channels must remain open starting from the handshake stage until the call is completed. The information that travels through these channels includes, at a minimum, the IP address and may extend to other information stored at the browser level.
The implementation of WebRTC technology in major web browsers such as Chrome, Firefox, Edge, and Safari has become a major concern among the VPN development community. It should be noted that many VPN users around the world live in countries ruled by repressive regimes. When people bypass surveillance and censorship, they need to remain anonymous while doing so for obvious reasons.
Even if VPN users do not conduct WebRTC conversations, their browsers may have this feature enabled, thus leaking their IP addresses.
DNS Hijacking
There is an even greater concern related to VPN and WebRTC. Domain Name Systems (DNS) are internet components that provide infrastructure services. They are enabled by means of special servers that operate at data networking levels higher than those of ISPs, and are tasked with routing and directing internet traffic. Basically, your computer or mobile device must connect to DNS servers whenever you need to access a website.
Even though DNS operations are decentralized, they can be compromised at either endpoint: your computer or the remote DNS server. Rogue DNS servers are routinely set up by authoritarian regimes to restrict web traffic, but they can also be operated by cybercrime groups to serve spam or to target unsuspecting users. A special piece of malware known as DNS Changer can compromise the security of your VPN sessions, and it can do so by means of a WebRTC call that you will not be able to detect.
Let's say you inadvertently visit a website that is serving DNS Changer malware. Once the malicious code executes, a JavaScript routine will place a WebRTC call for the purpose of revealing your IP address. Keep in mind that this can happen even if a VPN session has been previously established, but only if the VPN app is deficient in this regard. The next step of the attack consists of altering DNS settings so that you end up visiting malicious websites where you will be infected with even more dangerous malware.
To prevent such an attack, you (or your network operator) should limit the DNS resolvers permitted by computers in your organization’s network. There are two ways to accomplish this:
- Provide internal DNS resolver services
- Configure firewall policies for access to only known good DNS resolvers on the Internet. By doing so, DNS Changer malware will be prevented from successfully manipulating DNS resolution in the network.
Choosing a VPN
Even with all this talk about VPNs and data leaks, it’s still your best option for avoiding all the messiness of getting hacked. So how do you pick the right one?
There are hundreds of options when it comes to selecting a VPN. With the industry still in its infancy, they come and go with frequency. Some have impressive features and some not so much. If you do your research you’ll quickly see that some of the more popular VPN solutions will not keep logs of where you go online or leak your IP address or data.
When evaluating a VPN, pay close attention to what users are saying; Reddit and forums are good sources for intel. If you are interested in a particular VPN service which, after combing through various reviews and forum comments, only seems to leak when WebRTC is enabled on Firefox for Windows, then you should either stay away from Firefox or learn how to disable WebRTC.
Additionally, read through the privacy policy on a VPN service’s website, especially how they handle your data. Some take their users’ privacy seriously while others don’t think twice about selling your contact information to advertisers.
The Bottom Line
If you use a VPN, and you should, make it a point to check for data leaks. A VPN that leaks data is not worth a thing. Either test your connection yourself or hire someone to do it for you.
A final tip. When selecting your VPN service, look for something called a kill switch. It’s akin to the dead man’s switch on a train and will immediately interrupt your internet connection if the VPN fails for any reason. The theory here is that it’s better to be kicked offline than let your data be broadcast “naked.”