Security
Guide on How to Prevent Phishing
Phishing attacks (in which hackers send fake emails in an effort to trick users into clicking malicious links or giving away private information) have been around for decades. But they are constantly evolving, with new types of phishing attacks (such as spear phishing and clone phishing) targeting users.
It’s thus important to ensure that your strategy for combating phishing is constantly evolving, too. This article offers tips on how to prevent phishing. We’ll discuss how to detect phishing emails (or “phishes”), tools to help prevent phishes from reaching your end-users and best practices for educating users with the information they need to avoid falling victim to phishing attacks.
There’s no way to guarantee complete safety against phishing attacks. But by following the best practices described below, you can help minimize the risk that the end-users you support will fall for the phishes they receive.
For more information about phishing please refer to our guide on the topic:
Further reading Anti-Phishing Guide
How to Detect Phishing Emails
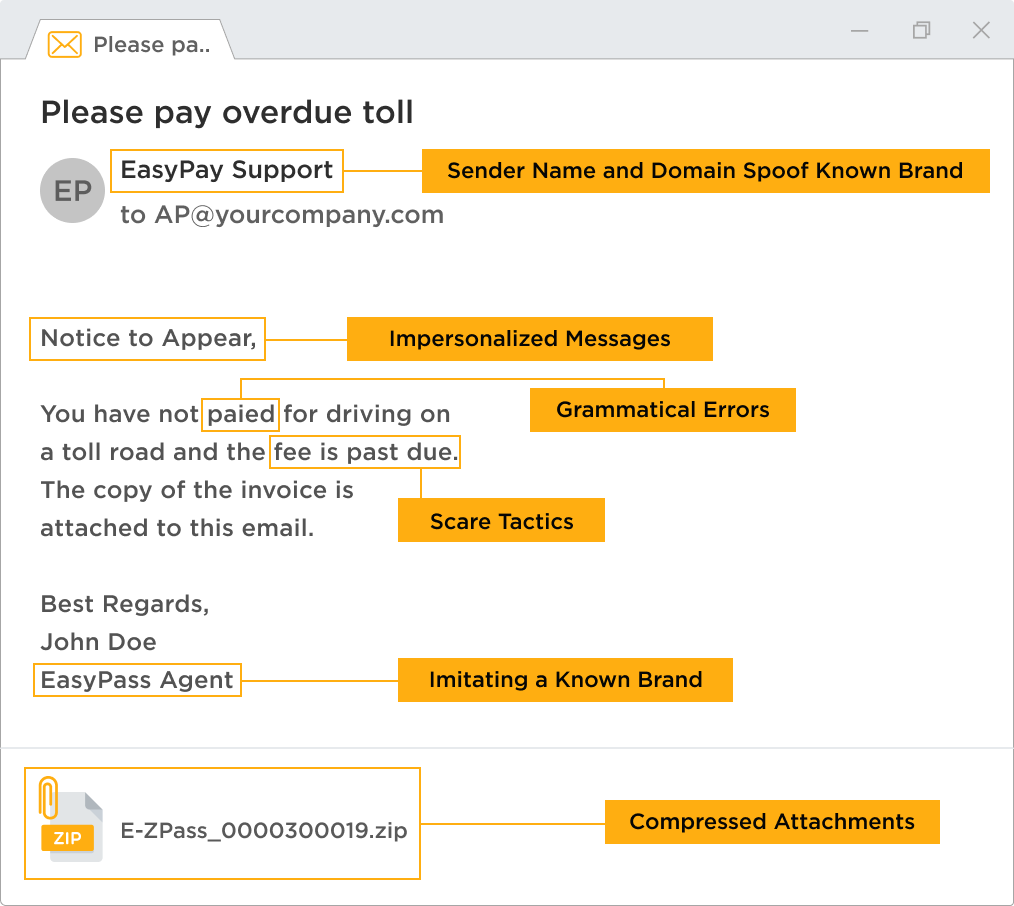
Even within phishing emails that look at first glance just like the real emails sent out by legitimate banks, application sites, and other sources, there are often clues that make it easy to identify the emails as phishes:
- The email asks for personal information, such as birthday information, a phone number, a social security number or mother's maiden name. Real messages should never ask for this kind of data.
- Misspelled words or bad grammar.
- They tell you you’ve won the lottery or some other contest, usually one you didn’t enter.
- The email asks you to make a donation for some heart-wrenching cause, to an organization with a name close to a real one, but slightly different.
- The email has a threatening tone or declaration of emergency. Phishes may say that an account has been hacked, that benefits are about to lapse, that you’ve been recorded through your webcam, or that there’s another threat already on your system. They often urge immediate action, in order to give the recipient less time to think.
- The email has attachments. (These may appear to be relatively innocuous, like PDFs or Word files, but they may, in fact, be applications that will plant malware.)
- The actual URL is different from the one shown. (A link may be underlined text or an image. Hovering over the link shows the actual URL that clicking on the link will take you to. If this doesn’t match the apparent sender of the message, it’s a prime indicator that the message is fake.)
How to detect phishing emails
How to Prevent Phishing
Anti-phishing systems scan for discrepancies between the apparent sender and actual sender, links that lead to known malicious sites, and malignant attachments. A good anti-spam system will block many phishes without having to scan the message for malicious content, simply because the apparent sender doesn’t match the actual sender, or because the actual sender is sending the same message to many users at the same time.
However, user training is still important even with a phishing scanner in place. Hackers are constantly trying to find new ways to get past filters. For example, they will set up new domains every day, and take down domains once the security vendors have identified them as fake. This constant change makes it difficult for security vendors to keep their signature files up to date.
Check out these marketing templates that we created to help MSPs sell Microsoft 365 as a managed service:

Deploying Internet Security Software
One important concept in security software is to have multiple layers. An antivirus app on the end user's system is not enough. A corporate firewall is not enough. An email filtering appliance is not enough. Any one of these systems may be bypassed by a new, sophisticated attack. The best approach is to use several layers of security, to keep them updated, and to train users regularly on new types of attacks.
Anti-Phishing Software
 Many firewalls (which may also be called UTMs or unified threat management systems) scan incoming email and look for security threats. The critical step for using a firewall to help combat phishing is to ensure that its anti-phishing functions are enabled and to keep it updated so that new types of phishing threats are covered as soon as the security vendor detects them.
Many firewalls (which may also be called UTMs or unified threat management systems) scan incoming email and look for security threats. The critical step for using a firewall to help combat phishing is to ensure that its anti-phishing functions are enabled and to keep it updated so that new types of phishing threats are covered as soon as the security vendor detects them.
Spam Filter
 Your email system, whether it is hosted by a vendor like Google or runs on an internal email server such as Microsoft Exchange or Linux Sendmail, has the capability to use spam filters that detect many types of email that pose a threat. This includes phishes, as well as emails with viruses and unsolicited commercial emails.
Your email system, whether it is hosted by a vendor like Google or runs on an internal email server such as Microsoft Exchange or Linux Sendmail, has the capability to use spam filters that detect many types of email that pose a threat. This includes phishes, as well as emails with viruses and unsolicited commercial emails.
These filters can also be used as separate appliances in conjunction with a hosted or internal email server. Under this approach, the mail is routed to the anti-spam system first, then on to the email server. Many vendors claim catch rates of 99% or higher for spam, but the more critical measurement is false positives. If users have to check their spam folder regularly for legitimate emails that have been erroneously blocked, they will not only waste a lot of time but will also have the opportunity to open phishing emails that have been blocked for good reason.
Antivirus Solution
 Install an antivirus solution, schedule signature updates, and monitor the antivirus status on all equipment.
Install an antivirus solution, schedule signature updates, and monitor the antivirus status on all equipment.
Good antivirus software is necessary. It will not only block phishes but stop other types of malicious content as well.
Further reading Top Antivirus Solutions for Managed Service Providers
Web Filter
 If a user does click on a link in a phish that is intended to take them to a site that will install malware or just make them think they’re logging into a legitimate bank or application web site, the web filter will block them from reaching the site if it has been identified as a malicious site.
If a user does click on a link in a phish that is intended to take them to a site that will install malware or just make them think they’re logging into a legitimate bank or application web site, the web filter will block them from reaching the site if it has been identified as a malicious site.
One thing to train users on regarding this topic is that they should trust the web filter. It doesn’t do much good to have the web filter ID a site as malicious if the end user bypasses the filter because they think it’s legitimate.
Two-Factor Authentication
 Two-factor authentication, or 2FA, adds a level of verification to user logins. Rather than simply requiring a username and password, 2FA sends a text message or another second factor to which the user must respond correctly before being able to log in. If a hacker has a user’s login username, and even their password, they will still not be able to enter a website because they won’t be able to get the second factor right.
Two-factor authentication, or 2FA, adds a level of verification to user logins. Rather than simply requiring a username and password, 2FA sends a text message or another second factor to which the user must respond correctly before being able to log in. If a hacker has a user’s login username, and even their password, they will still not be able to enter a website because they won’t be able to get the second factor right.
Like all other security solutions, 2FA can be bypassed by clever hackers, so it’s not a set-and-forget function; it is simply another technique to add an additional layer of security.
Further reading Two-Factor Authentication: Solutions, Methods, Best Practices
Password Management
 In addition to having virus protection software on your computer, it is crucial to use a password manager to manage your online credentials.
In addition to having virus protection software on your computer, it is crucial to use a password manager to manage your online credentials.
Rather than having a user type in a password each time they visit a site, a password manager stores the passwords in a secure database. When the user goes to the login page for a given website, the password manager will fill in the username and password. Since the password manager stores the login information for each site separately, a site whose URL is close to that of the correct site, but not an exact match, will not have login information stored. This gives the user another clue that something is wrong.
Phishing Prevention Best Practices
The single most important anti-phishing practice is to assume that all security solutions are temporary. As happened to the Maginot Line, eventually hackers will go around existing security systems. The systems must, therefore, be updated regularly and supplemented with additional tools regularly.
Here are some best practices and tips on how to prevent phishing:
- Encrypt all sensitive company information. This should occur at several levels – encryption of database records, encryption of files on your systems, encryption of all data stored in the cloud, ensuring that service providers encrypt company data that they are storing on their systems, and ensuring that data stored by partners or vendors is also encrypted. Many of the recent highly publicized leaks have occurred because a third party stored a password file that wasn’t encrypted, or placed data in the cloud without properly encrypting it.
- Make sure all traffic that flows between your company and other websites is encrypted with SSL or TLS. Make sure that your SSL certificate is up-to-date and that it uses a high number of bits (at least 1024, although 2048 or more is suggested), as well as with 256-bit encryption).
- If you’re taking payments from customers via the web, use something like Elavon’s secure hosted payments to protect your customer’s data. Make sure your provider has up-to-date PCI DSS and ISO 27001 certifications from independent auditors.
- Require encryption for employees who telecommute. This is another attack vector that can be secured via encryption: Don’t just secure your internal systems, but make sure that any user who connects from outside the system is secure while accessing your system.
- Keep all systems current with the latest security patches and updates. As hackers and their attacks are constantly evolving, so to must your security systems.
- Be cautious about your employees accessing your network via public wifi connections. Wifi set up at airports, coffee houses, or retail establishments may not be encrypted, making it easier for hackers to intercept web traffic or emails and trace login information, passwords or certificates that are used to access your network.
- Beware of shortened links. Shortened links do not show a website’s real name and hence, they can be more easily used to trick the recipient into clicking them. Users should be trained to be skeptical of shortened links.
- Verify the target site’s SSL credentials.
- Make sure your endpoint security software stops malicious pop-ups. Pop-ups may be initiated by ads from a third-party site and can redirect a user to a different site, or capture personal information using iframe technology.
- Verify the target site’s SSL credentials.
- Check read up on the evolution of malware. Since hackers are constantly refining their techniques, it behooves the security manager to do the same. Sites include ones that cover security in general, like www.darkreading.com and security vendor sites like www.symantec.com and www.fortinet.com.
Employee Education on Phishing Prevention
The education of employees is a critical element of phishing prevention. Employees should be aware of the dangers of clicking on a dangerous link in an email. It is critical to educate all employees and do it regularly.
Unfortunately, many upper-level employees may believe themselves to be too important to attend training, too smart to fall for hacker’s tricks. Those employees also tend to have access to sensitive data or banking sites. This is why many spear-phishing attacks target these employees specifically. Some examples of the millions of dollars that other companies have lost in these types of attacks may go a long way toward gaining their attention.
Phishing awareness education should be:
- Short and engaging. The old KISS (Keep it Simple, Stupid) principle works here – regular emails that cover one or two new threats are better than a quarterly 10-pager.
- Regularly delivered. Consider the turnover. Phishing awareness training should be part of the employee's orientation program. (Most experts recommend that you administer phishing protection training every two months.)
- Progression tracked. Show what you’re doing to protect corporate systems and how threats are continuing to evolve.
- Relevant to the modern-day. Don’t use articles from ten years ago. There are enough fresh examples.
There are some more best practices of employee education on phishing prevention:
- Teach your employees what a phishing email looks like, how to spot fakes and what to do when they get one.
- Tell your employees to come forward and report possible attacks when they think they’ve received one.
- Periodically make your employees aware of successful phishing attacks that have happened in your industry.
- Perform phishing attack simulation. Create a third-party email address and send out emails from time to time to see if you can catch anyone clicking on links when they shouldn’t.
- Don’t leave out upper management. They need to be just as ready as the rest of your company and (as noted above) they are often specifically targeted by spear phishes and clone phishes.
- Print out the list of things to look for and have your employees keep it at their desks somewhere where it will be easy to see.
Summary
Phishes and other types of malware can be stopped, but you can’t put up a wall and assume it’ll be secure for the foreseeable future. Just as hackers are constantly working to bypass security systems, your security systems and techniques must constantly evolve to counter the new threats.