Like most modern operating systems, Ubuntu Linux is designed to be secure by default. However, also like most modern operating systems, Ubuntu can be made even more secure through security hardening.
This article provides an overview of Ubuntu security hardening best practices. The Ubuntu security hardening tips below should apply to any version of Ubuntu released in the past few years, but we'll focus in particular on Ubuntu 18.04, the latest "long-term support" version of Ubuntu.
Minimal Ubuntu Software Selection
On modern versions of Ubuntu, there are about 50,000 individual software packages that you can install on your system. Each package provides an application or part of an application.
Most Ubuntu installations don't require anywhere close to all of these packages, however. And every package that you have installed but are not using creates unnecessary security risks.
Therefore, you can harden your Ubuntu system by minimizing the number of applications you have installed. Ideally, you'll do this during system installation time. This is easy to do on Ubuntu Server Edition, which lets you pick and choose different categories of packages to install, as the screenshot below illustrates:
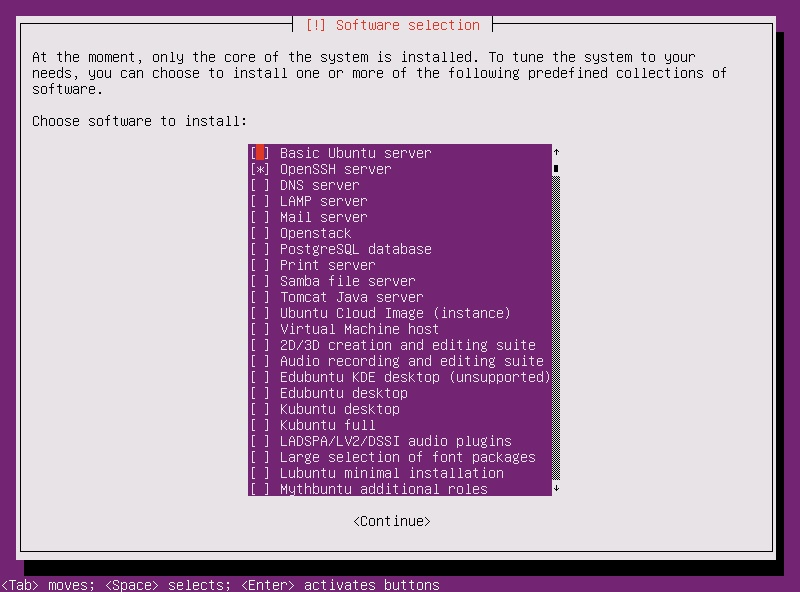
Other editions of Ubuntu provide less freedom to customize which packages are included with the installation. However, you can easily remove unnecessary applications in the Ubuntu Software Center (Ubuntu's graphical software-management tool) or via the iap-get command-line tool.
Disk Encryption and Ubuntu Security
Another Ubuntu security hardening best practice is to encrypt your hard disks. That way, if someone gains unauthorized physical access to your systems (by stealing your laptop, for example), they won't be able to read your data.
On desktop editions of Ubuntu, you can easily choose to encrypt the system during installation using a convenient graphical interface:
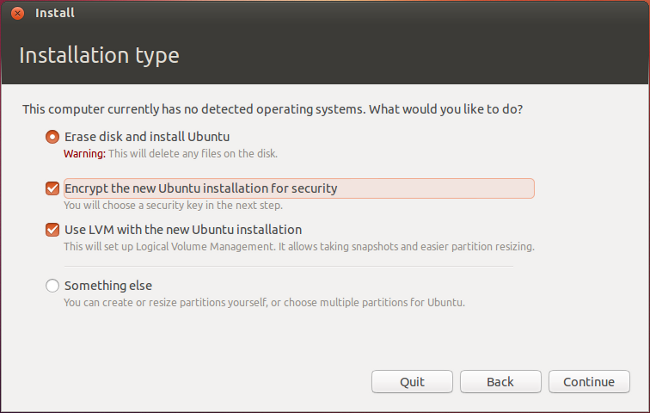
And even if you've already installed your Ubuntu system without encrypting it, you can still encrypt it. See the Ubuntu disk encryption documentation for instructions. Keep in mind that it's a best practice to back up your data prior to applying full-system encryption, just in case something goes wrong during the encryption process.
Remember, too, that because Ubuntu decrypts your disks when it boots, disk encryption will only protect data in a system that is not running. It does nothing to prevent an attacker from accessing your data if they are able to gain physical or remote access to the system while it is actually turned on.
Firewalls and Ubuntu Security Hardening
To harden your Ubuntu system against attack from the network, you should set up a firewall. By default, most editions of Ubuntu come with a built-in firewall tool called ufw. (Technically, ufw is not a firewall; it's just an interface for iptables, the Linux kernel's main framework for controlling access to network ports and hosts. But most end-users don't need to know the difference.)
However, even though ufw is installed by default on most Ubuntu systems, it doesn't do anything until you tell it to. A simple ufw configuration that will harden your system is to run these commands:
sudo ufw default deny incomingsudo ufw default allow outgoing
This tells ufw to block all incoming network connections (like someone trying to log into your computer remotely or access files over the network) and allow all outgoing connections (such as your Ubuntu system connecting to a remote application).
You can then use ufw to enable specific types of incoming connections as needed based on the connection protocol (like TCP or RDP), the port number and/or the IP address where the request originates. For example, if you want to enable SSH connections (which use the TCP protocol on port 22 by default) from the host 192.168.1.10, you could run this command:
sudo ufw allow from 192.168.1.10 to any port 22 proto tcp
This would be useful if you want to block all SSH requests by default, but allow requests from a specific workstation (with IP address 192.168.1.10 in the example above) that you use to administer your Ubuntu server.
Hardening Your Ubuntu System with AppArmor (or SELinux)
AppArmor is a security hardening framework designed for Ubuntu that lets you place restrictions on how individual programs can behave, and which system resources they can access. The intended purpose of AppArmor is to mitigate the extent of a breach by ensuring that even if attackers are able to take control of some of the software on your computer (by, for example, convincing you to install malware on the system), the damage they can do will be limited because the software won't have free reign to do whatever it wants.
AppArmor is a complicated tool, and a full explanation of how to use it is beyond the scope of this article. In a nutshell, however, you first need to install AppArmor (it's not installed by default on most Ubuntu systems), then create profiles that control how different applications can behave. The Ubuntu documentation offers more details.
On most Ubuntu desktop systems, AppArmor is probably an overkill. It is probably not worth learning to configure AppArmor if you are just a regular PC user. On Ubuntu servers, however, taking the time to learn to work with AppArmor is a smart way to harden your system against attack.
You may hear people talk about SELinux as an alternative to AppArmor. SELinux is a similar framework that is popular on Linux distributions other than Ubuntu. SELinux can be installed and used on Ubuntu systems just as well as AppArmor; however, AppArmor is the framework that Canonical (the company behind Ubuntu) favors. So, unless you already know how to work with SELinux, it's generally a good idea to choose AppArmor as your security framework on Ubuntu, because AppArmor is better integrated into Ubuntu.
Data Backup and Ubuntu Security
Last but not least, backing up your data is an Ubuntu security hardening best practice. While data backups won't make your system harder to attack, they will help ensure that if attackers do breach it, you'll have clean data from which you can restore the system.
Further reading How to Backup Ubuntu to the Cloud with MSP360 Backup
There are various open-source tools that you can use on Ubuntu to back up data; for a list, check out the Ubuntu backup documentation. However, most of these tools require a fair amount of effort to configure, especially if you want them to run automatically. Some also only work on the command line.
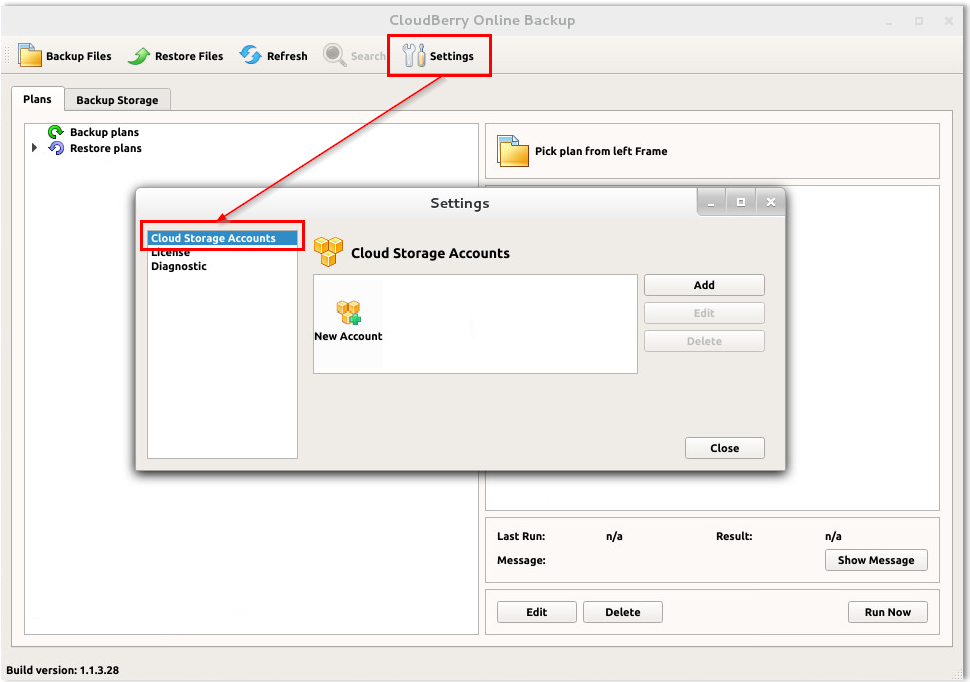
If you want a simpler backup experience that includes easily automated cloud backups and a graphical user interface, check out MSP360 Backup for Linux (pictured above).
Conclusion
A variety of Ubuntu security hardening tools and techniques are available to make your Ubuntu system even more secure than it is by default. Depending on how mission-critical your Ubuntu system is, and how sensitive the data it stores may be, following the Ubuntu security hardening best practices described above can be a wise investment of your time, because it will help prevent attacks and data breaches.





